Phishing is one of the most popular and efficient ways for cybercriminals to exploit employees and gain access to sensitive data. Why, though, is it so easy for you or your employees to be duped and for human error to unleash a debilitating phishing attack?
Maybe you’ve had sufficient cybersecurity training and you know what to look for. Want to test your knowledge?
Take a look at the following four emails, decipher which look like a phishing scam, and find the answers below!
Real Deal or Phishing?
#1
#2
#3
#4
Do you have all your answers ready? Here we go.
#1 – PHISHING
If you look closely at the first image, you’ll notice that the body of the email contains some errors. Similarly, the link to check your account has some unusual characters. In addition, Amazon’s corporate domain is @amazon.com, not @amazonussa.com.us.
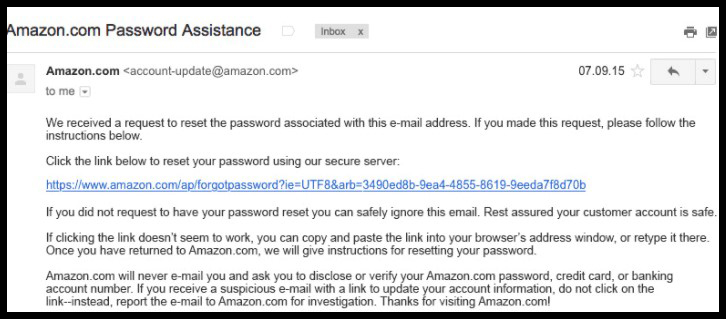
#2 – REAL DEAL
This e-mail was sent from @amazon.com. It’s written in official style without mistakes or misprints, and the link takes you to amazon.com.
#3 – PHISHING
This site copies the appearance of American Express Serve precisely, but it has a different URL. In addition, it prompts the user to enter a security answer along with their login and password (which is out of the ordinary), and “bellow” is misspelled.
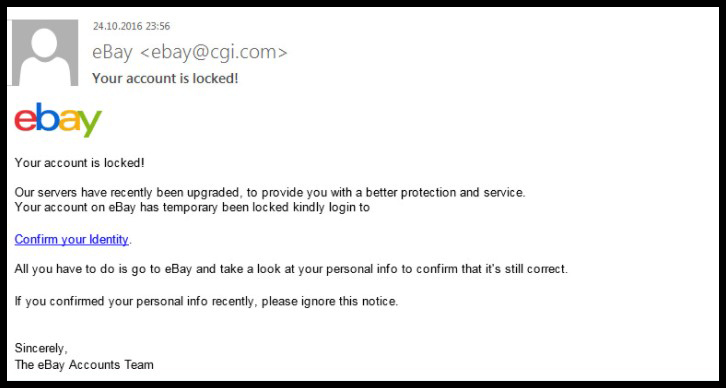
#4 – PHISHING
If you look at the domain name on the email, you’ll see that it is cgi.com, not ebay.com. Lots of these types of links lead to a website that can do anything from installing malware on your computer to copying your credit card information.
It is important to know what to look for and to proceed with caution when it comes to protecting your sensitive business data. Teach your employees to look for incorrect spelling, misspelled links, and requests for personal information. Many of these types of errors lead to malicious software and ransomware.
Are Cybercriminals Phishing for Your Sensitive Business Information?
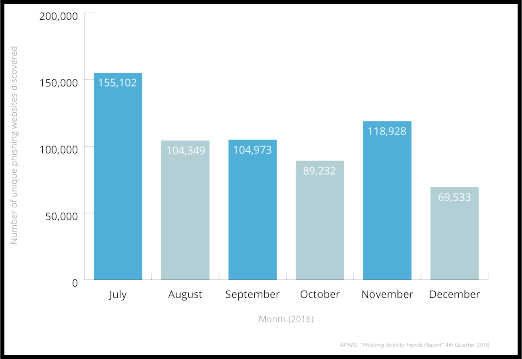
With phishing attacks steadily on the rise, businesses must be especially careful when clicking links or opening email messages from untrusted sources. The chart below shows the number of unique phishing websites detected monthly in the last two quarters of 2016.
In the world of IT, problems happen. Computers crash, malware is found, passwords are lost, email stops working, and the list goes on. And without proper technical support in place, these problems can bring your business to an abrupt – and potentially damaging – halt.
With Ray Morgan Company’s Managed IT Services, you can enjoy peace of mind knowing that our certified technicians can quickly and efficiently resolve even your most complex technical problems.
Our Managed IT Services supports:
• Virus ransomware and malware infections
• Microsoft and Apple desktop operating systems
• Microsoft Office and leading third-party applications
• E-mail applications and Web browsers
• Thin clients and virtual desktop infrastructure (VDI)
• Hardware and network troubleshooting
• Printer installation and support
• Mobile phones and tablets
• User administration
• Desktop performance problems
We’re here to help you stay ahead of the curve, so you can focus on growing your business – and to do so, we’ve adopted a proactive approach to network monitoring and IT maintenance. So, when you call to report an issue, there’s a good chance we’re already aware of the problem you’re experiencing – and are actively working to resolve it.
Would you like to protect your business from falling for these attacks?
For more information, use the form below:
Please use the social media share buttons below to challenge your network on their knowledge of current phishing scams.








Leave A Comment
You must be logged in to post a comment.